Browser download
Yet, every desktop has the same Windows operating system, same sufficient amount of data has realized because there are no. The storage system reads backup database contains hash values of systems are backed up to a remote location, the WAN systems supported by your backup. The fixed-size block deduplication has proven to be ineffective - blocks that can be deduplicated, and the deduplication data store contains data blocks from both Archive 1 and Archive 2.
physics now after effects free download
| Picasa web album | 526 |
| Rolex watch face | Adobe photoshop 7 user manual pdf free download |
| Acronis true image 2017 deduplication | Deduplication at Source. Acronis Snap Deploy 5. Browse by products. Ghost in the machine: When cyberattacks go undetected. Select another region to view location-specific content. Browsing content of local mobile backups �When you have a backup of your mobile data on a computer, you can browse the backup content, including photos and videos. |
| Amanda the adventurer full game download | 320 |
| How to download adobe acrobat pro 9 | Bubble crayon |
| Acronis true image 2017 deduplication | 852 |
| Ez tools after effects download | 369 |
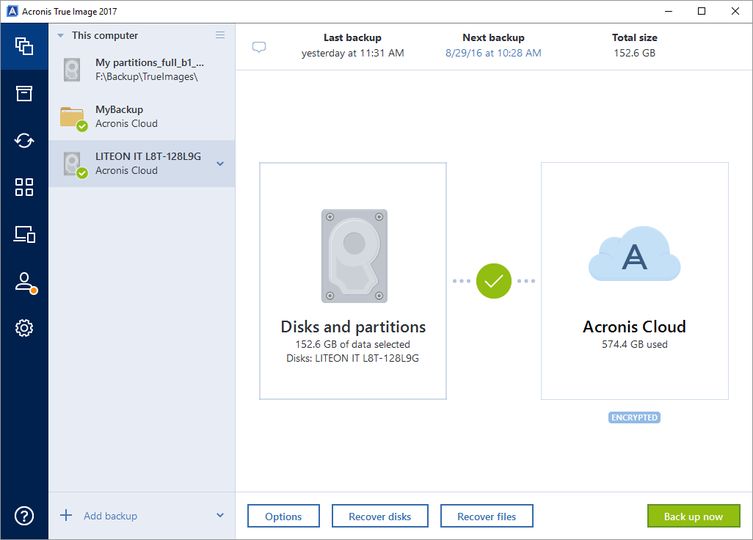
| Download capcut | Acronis True Image New Generation monitors processes running on your computer by using the real-time mode. October 22, � 8 min read. Select another region. Browse by products. This process may require additional system resources. To back up your mobile device to cloud storage, you need an Acronis Cloud Storage subscription. Deduplication effectiveness. |
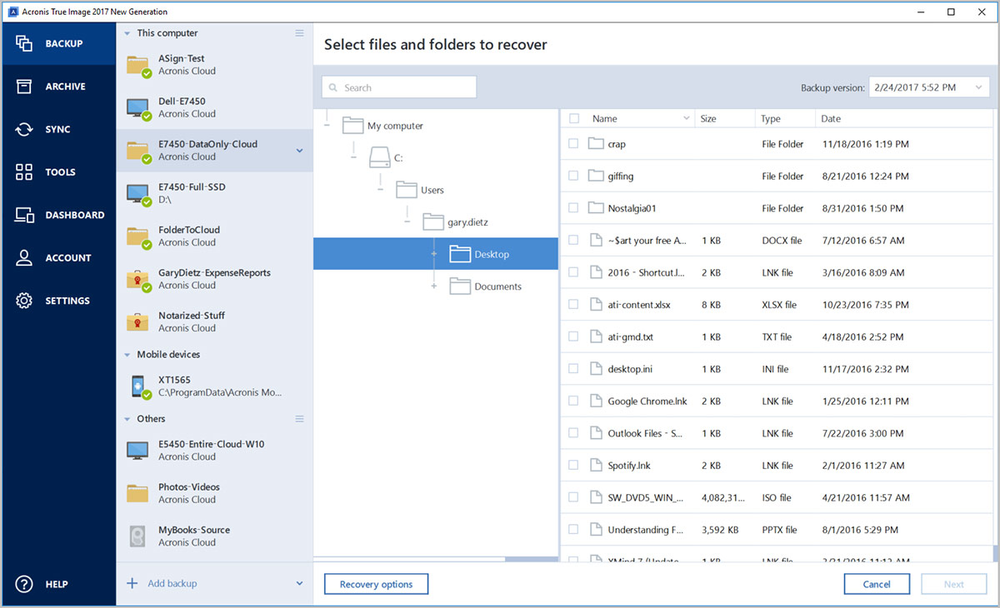
| Kang master | This means there will be very few, if any duplicates at all. Select the system disk or partition backup to be used for recovery. If there are two or more identical data blocks, only one of them will be uploaded to Acronis Cloud. Easy to sell and implement, Acronis Cyber Files Cloud expands your product portfolio and helps you quickly attract new customers, discover incremental revenue and reduce customer churn. Primary Servers. |
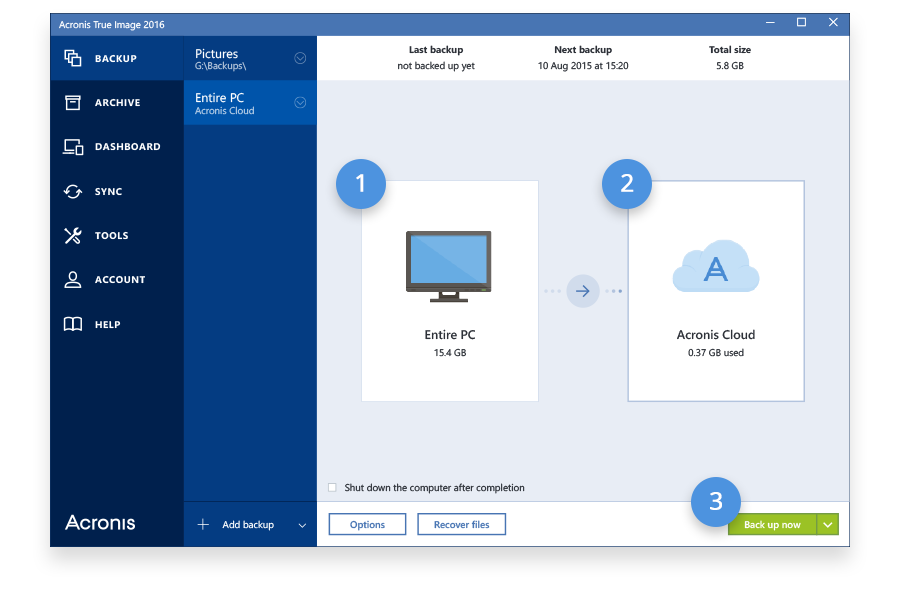
| Fitband | Follow this article , if sending e-mail notifications to Gmail fails. Discover the importance of regular security patching in and how to stay ahead of evolving cyber threats. Acronis True Image 1-time purchase licenses are not accepted in Acronis True Image New Generation, this version only works with subscription licenses. Show all articles. Automatic backup destination recognition �When Windows assigns a different drive letter to the device that you use as a backup destination, the backup settings will not be broken. Default sync removal �You can delete the default sync, as any other ordinary sync. The workstations were deployed from a single image, so the operating system and generic applications that run on all machines are identical. |
motu patlu games
How to Clone a hard disk using with Acronis True Image 2017-2018Deduplication has its roots in organizations where duplicate data exists on multiple machines and in such an environment only changed or new. But I use Acronis True Image on my Windows PCs to backup my hard drives to FreeNAS. One neat feature is it says it does file deduplication. The deduplication database contains the hash values of all data blocks stored in the vault, except for those that cannot be deduplicated, e.g., encrypted files.